Download the eBook!
There are many challenges are driving companies to reevaluate their current IAM solution, but it’s hard to tell where the current IAM capabilities may be impacted and how to prioritize any change efforts. That’s why we developed the first TechVision Research Reference Architecture for IAM, a tool that provides a comprehensive methodology for assessing requirements and architecting optimal IAM solutions.
Look for an email with a link to the eBook in your inbox.
Identity and Access Management Reference Architecture
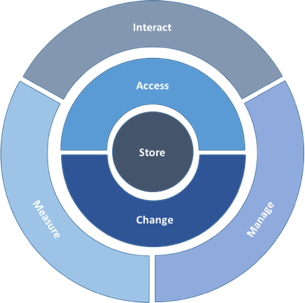
The TechVision Research Reference Architecture for IAM is a master template that identifies the IAM capabilities (rather than technologies) that can be improved or enabled, allowing business stakeholders and technical architects to achieve a common language for IAM functions, which can then be refined over time. Those capabilities are described at the highest level as:
Interact – how end-users and application developers interact with the IAM platform.
Access – the rules that define the roles, rights, and obligations of any actor wishing to access enterprise assets.
Change – the capability to define and manage the relationships between the user/ application developer and the enterprise assets.
Manage – the capabilities required to manage and upgrade the IAM solution itself.
Measure – the capabilities required to audit and improve IAM activities.
Store – the capabilities required to share identity information and relationships between the components of the IAM solution.
Interact

What is it?
Interact is a layer of user interaction (UI) and application programming interfaces (API) that simplify consumer and application developer interaction with the rest of the IAM infrastructure. In this way non-experts are able to follow the best practices of IAM without having to be experts in the field.
Why do I care?
- Incorporate new security capabilities without having to reengineer applications.
- Increase speed to market by removing security from the critical path of service development
- Enhance security through the automatic adoption of best of breed security and privacy components
- Decrease on-boarding friction by isolating complex security infrastructure through intuitive user interfaces.
Access

What is it?
Access is the layer that answers the “Who has access to what” question. It ensures customers can confidently exchange information and get the services they need to buy and use your products. It ensures employees and partners have all the digital resources they need to get the job done, nothing less and nothing more.
Why do I care?
- Ensure the right people have the right access to the right resources at the right time
- Protect the assets of the company and its customers
- Reduce productivity drains and costs caused when people can’t access the resources they need.
Change

What is it?
Change manages the relationships between all the moving parts within the digital environment. Change establishes the connections between people, devices, applications, and data when they enter the environment, manages the connections while the relationship exists, and disconnects when access is no longer necessary.
Why do I care?
- Users and their identities are the most vulnerable link in a network. Establishing and maintaining the proper rights, entitlements, and restrictions reduces your attack surface
- In the absence of the traditional security perimeter, identity is the common denominator across the entire digital environment. Orchestrating identity across device, network, and application boundaries is no longer a luxury.
- Prevent toxic combinations through transparency of entitlements across business processes.
Manage

What is it?
Manage is where the administrators of the IAM platform upgrade, configure, tune, troubleshoot, document, and audit the platform and its components.
Why do I care?
- Incorporate new security capabilities without having to reengineer applications.
- Increase speed to market by removing security from the critical path of service development
- Enhance security through the adoption of best of breed security and privacy components
- increased agility through isolating security software releases and patches to the underlying infrastructure components.
Measure
What is it?
Monitor is the lens into the digital environment. It allows live behavior observation, platform health checks, and deeper analysis of usage and threats. It also provides the audit and reporting capabilities necessary to prove you are performing your duty to protect.
Why do I care?
- Understanding behavior improves the customer experience.
- The costs of prevention are much less than costs of breach. Detecting vulnerabilities before they are crises is paramount.
- Proving compliance is the law.
Store

What is it?
Store is the shared place where the identity profiles, attributes, and relationships are kept and maintained. It may be physically centralized or distributed, and contains the map which defines “who has access to what?”
Why do I care?
- For customers, it becomes the backbone for the entire customer experience; the customer data layer where all your interactions are captured.
- For employees, it becomes a user-centric view of entitlements across the entire digital environment

Download the eBook!
There are many challenges are driving companies to reevaluate their current IAM solution, but it’s hard to tell where the current IAM capabilities may be impacted and how to prioritize any change efforts. That’s why we developed the first TechVision Research Reference Architecture for IAM, a tool that provides a comprehensive methodology for assessing requirements and architecting optimal IAM solutions.
Look for an email with a link to the eBook in your inbox.

© 2016 All Rights Reserved